Your Intelligence-Driven Defense Hub
Built for modern defenders, Unit6 transforms noisy threat feeds into crystal-clear, prioritized action. Empower your security, IT, and risk teams with one platform that reveals what attackers are really after—so you can fix what matters first, fast.
Better Intelligence = Stronger Security
See your environments through the enemy’s eyes

The signal you need, not the chaos you don’t.

Intelligence that fits your workflow, instantly.

Focus only on threats attackers are actively preparing to exploit—so your team works smarter, faster, and with confidence.
Reveal the attacker’s playbook with intelligence sourced from their own infrastructure—uncover risks traditional tools miss and act before threats materialize.
Unit6 delivers the experience of elite threat intelligence teams—automated, scalable, and embedded directly into your workflow when and where you need it most.
The Preventive Intelligence™ Platform
Why Unit6 Outperforms the Rest
| Features |
Unit6
|
Legacy Companies
|
Other Competitors
|
|---|---|---|---|
| Real Attacker Signals |
|
|
|
| Predictive Threat Detection |
|
|
|
| Prioritized, Actionable Alerts |
|
Limited
|
|
| Fast, Zero-Friction Deployment |
|
|
Limited
|
| Built for Prevention, Not Reaction |
|
|
|
| Native and Seamless Integration |
|
Limited
|
Limited
|
How We Collect Intelligence: A Unified, Multi-Layered System
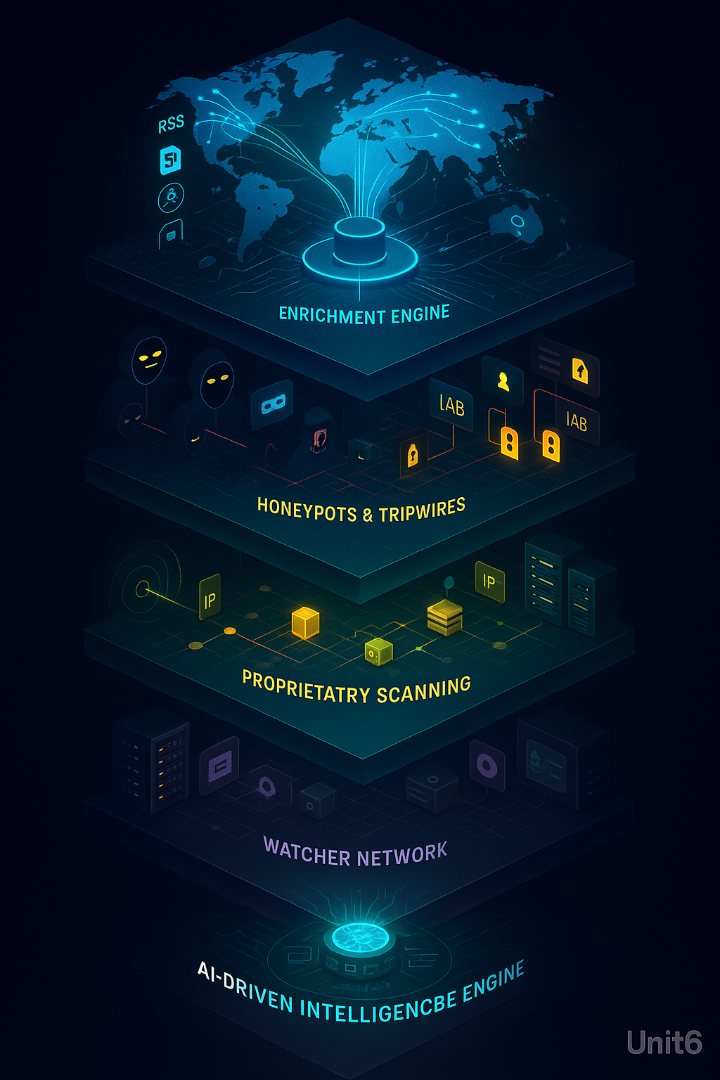
Automated Open Source and Feed Aggregation

We developed proprietary automation pipelines that collect and enrich data from:
- Open-source intelligence (OSINT)
- Commercial and community threat feeds
- Public malware repositories and sandbox reports>
Our enrichment engine cross-validates this information with other signals, detecting threats traditional systems often miss due to volume or context gaps.
Covert Persona Networks and Forum Infiltration

We developed proprietary automation engine that manages a fleet of automated online avatars - high-reputation digital identities embedded in invite-only cybercriminal forums, encrypted chats, and underground marketplaces.
This access allows us to:
- Identify imminent threats, such as when a customer has already been compromised
- Track new IAB listings, targets, and monetization trends
- Intervene early, before access is sold or used for ransomware deployment
Honeypots and Tripwires

We’ve long maintained a global mesh of honeypots and digital tripwires.
These assets generate long-tail signals including:
- Real-world malware samples
- CVE exploitation trends and zero-day activity
- Botnet communication patterns
This time-tested infrastructure provides rare longitudinal insight into evolving TTPs (tactics, techniques, procedures) as well as existing and new threat actor groups.
Proprietary Global Scanning
We use two primary types of active scanning, each designed to uncover different layers of malicious infrastructure and adversary behavior across the internet.
- Strategic, Actor-Focused Scanning Automatically maps newly registered threat actor assets by correlating behavioral patterns with known and emerging signatures.
- Full-Internet Sweeps Powered by a proprietary high-speed scanning engine trained on adversary behavior and unique signatures. Combined with our in-house AI model, this approach rapidly uncovers malicious infrastructure even when attackers are actively trying to evade detection.
The Watcher Intelligence Network

Our Watcher Network is a proprietary passive collection system embedded deep inside threat actor environments - from internal communications to tools and everything in between. This access is the result of strategic placements and access.
It enables us to:
- See internal targeting in real time
- Observe what attackers scan, exploit, and prioritize
- Detect changes in targeting intent before an attack occurs
The Autonomous Intelligence Engine Behind It All
All signal sources converge into a custom-built AI engine powered by autonomous agents that continuously ingest, analyze, and act on data across five key modalities - technical indicators, infrastructure patterns, and adversarial chatter.
These AI-driven agents operate independently to correlate cross-domain signals and take proactive steps in real time. This enables us to:
- Predict attacker behavior based on multi-source telemetry
- Attribute infrastructure to threat actors with high accuracy
- Deliver Preventive Intelligence—a dynamic view of how attackers perceive your environment and what they’re likely to do next
